Microsegmentation
Buyer’s Guide 2025
Discover how identity-based microsegmentation protects users, workloads, and devices with granular, context-aware policies. Download the Buyer's Guide and Checklist.
Download the Buyer’s Guide


Get Your Comprehensive Microsegmentation Buyer’s Guide
Dive deeper into the critical need for microsegmentation, evaluation criteria, key features, implementation considerations, and how to build a business case. This guide provides the insights you need to make an informed decision.
- Understand the evolution from perimeter defense to Zero Trust.
- Discover key success factors for selecting the right solution.
- Learn how to navigate deployment and integration.
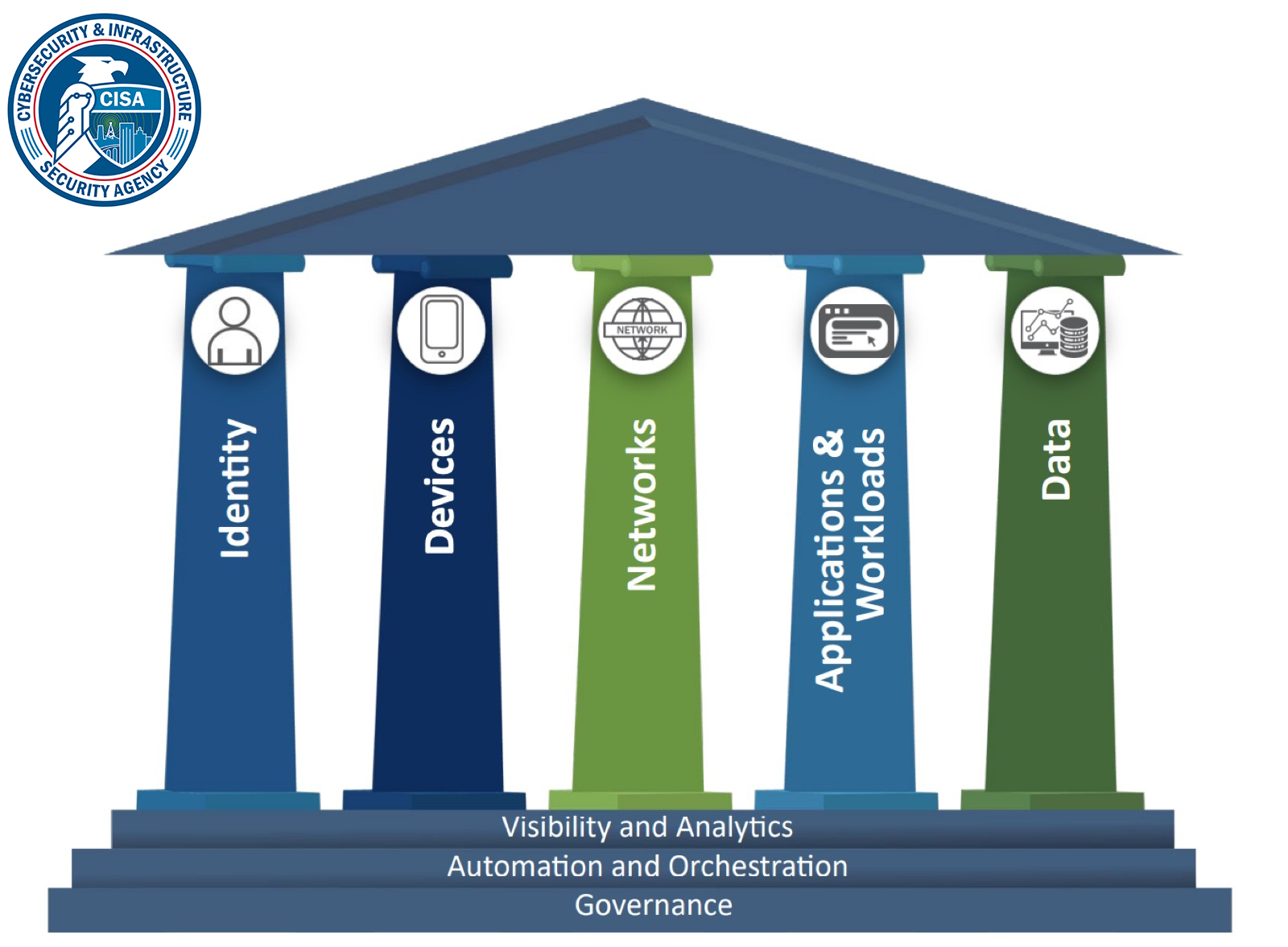
What is Microsegmentation?
Identity-based microsegmentation enables organizations to rapidly secure their networks by applying granular, context-aware least-privilege access policies that automatically protect users, workloads, and devices wherever they appear on the network — preventing lateral movement attacks while eliminating the need for new hardware, agents, or complex network reconfigurations.
Why Modern Microsegmentation is Critical Today
- Cybercriminals increasingly leverage lateral movement (east-west traffic) after initial access.
- The explosion of IoT, OT, and IoMT devices expands your attack surface, often with legacy software that traditional tools can't secure.
- Did you know? 60% of successful breaches involve lateral movement, with attackers often going undetected for months.
- Traditional segmentation (VLANs, firewalls) creates operational overhead and leaves security gaps, especially where agents can't be deployed.

The Business Value of Microsegmentation
- Reduce Breach Impact: Significantly lower breach costs (typically 45% lower) by limiting lateral movement.
- Lower Operational Costs: Achieve a 60%-80% reduction in policy management overhead and operational costs.
- Faster Incident Response: Decrease incident response times by 40%-60%.
- Strengthen Compliance: Simplify audit preparation for standards like IEC 62443, HIPAA, and NIST Zero Trust.
- Potentially Lower Cyber Insurance Premiums: Documented security controls can lead to 15%-30% reductions.



